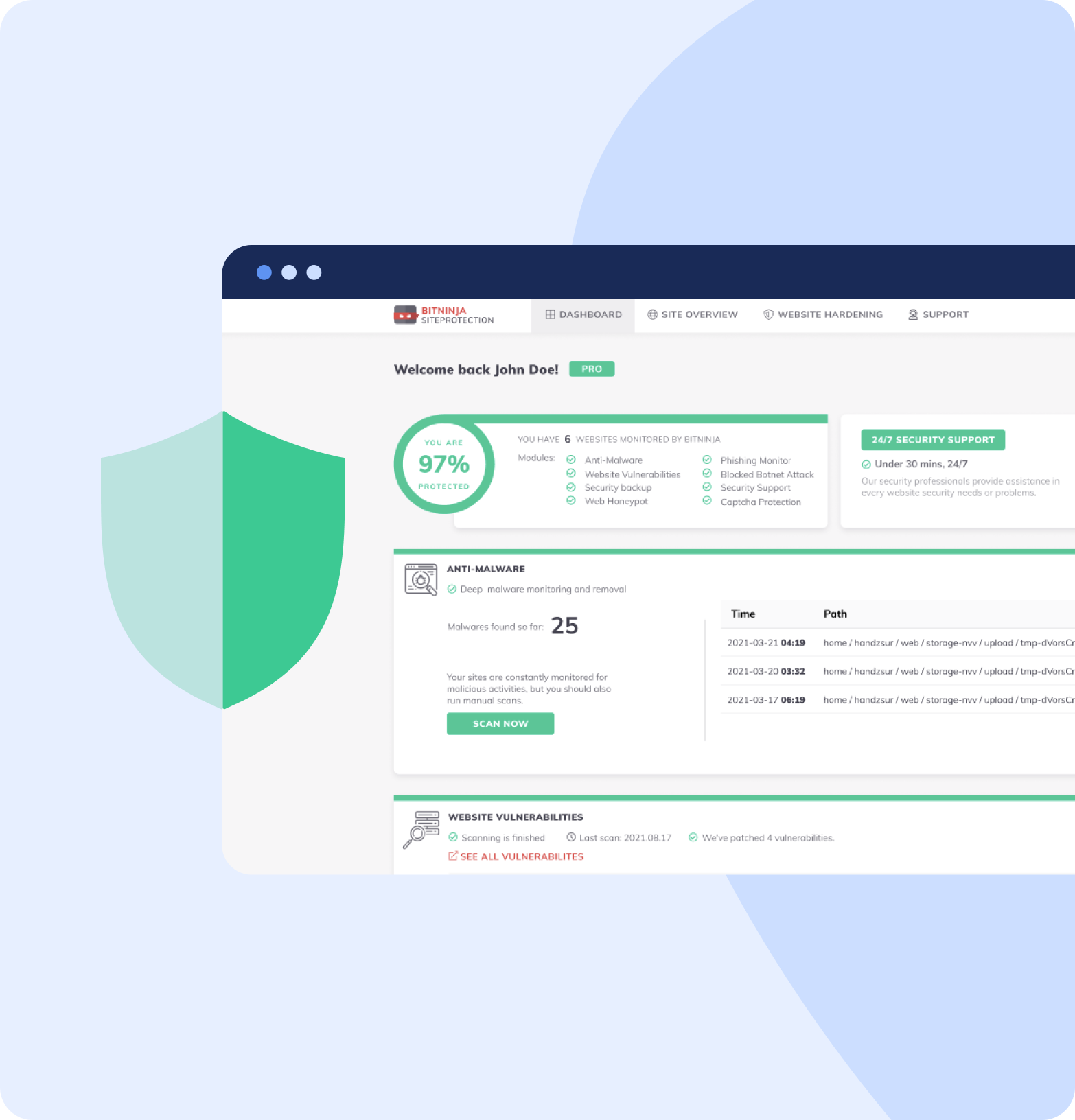
What is also surprising is that BitNinja collects not only information but also learns from them. That's how this technology guarantees a low false-positive rate: 0,1 %. This software is very friendly with other software. For example, it works well combined with Webhosting software and virtual solutions: Cpanel, Plesk, Apache, Nginx, etc.

Features
Realtime IP reputation
Highly developed Botnet Protection which not only blocks access to malicious domains to limit the risk, it also prevents infected systems from connecting back to the botnet's control servers. It works in the deep of your OS, so you will not notice when BitNinja is working.
DoS detection
BitNinja can supervise the number of established connections, and can intervene if the active connection number exceeds the limit. By default, the limit is 80 connections per minute. Although, every user can personalize their own settings.
Log analysis
This module is called in our nomenclature SenseLog. This automatic module is responsible for analysing log files (apache2 access logs and error logs, auth log, exim4 and control panel login logs, MySQL, Nginx, Post-fix, PureFTP and VSftp) and takes the necessary actions.
WAF
WAF is implemented to protect your servers from the most common attacks like cross-site scripting, SQL injection, buffer overflowing, or data thefts. Web application firewalls (also known as the proxy-based firewall monitor, filter and block incoming traffic on HTTP protocol in real-time.
Honeypots
Honeypoting is a really effective way to catch bots. They fake a real service on the page, but they are only there to entrap malicious bots. Web honeypots are hidden on the most unattainable parts of the webpage, so human visitors normally cannot reach them. Please note that you have to place the honeypots manually, but we can provide the scheme that you can use.
Malware detection
Our up-to-date detection technologies are combined with traditional methods to help increase the efficiency of malicious object detection and support proactive protection against new hostile programs. As a first step, malware will be placed in quarantine, secondly, the place where it was located will become a honeypot.
Frequently Asked Questions
Where can I find more information?
Our support team is glad to help you 24/7 via chat.
What is BitNinja?
BitNinja is an easy-to-use server security tool, which can be installed on your server within a couple of minutes and requires virtually no maintenance. It is a mixture of an on-premise and cloud-based solution. With its agent which sits on your infrastructure and sends the attack information to the central server which is in the cloud.
Can I use cPanel on Windows?
cPanel was built only for the Linux environment and doesn’t support any Windows OS and its distributions. Although more experienced users use backdoor methods to run this software on Windows servers, for convenience’s sake it is generally advised to use alternative control panels, like Plesk.
What is the difference between cPanel and Plesk?
Both are popular web hosting control panels. While they do offer similar features, there are some core differences:
- Distribution compatibility. Plesk is available for Windows, Linux, and 14 Linux distributions, including RedHat Enterprise, Ubuntu, CentOS, and Debian. cPanel is only available for Linux OS.
- Interface. Plesk is streamlined for first-time users and groups features in a list on the left side of the window offering a tidier interface. cPanel does not group similar tools & features but it allows you to customize the home screen.
- Extensibility. Plesk already comes installed with various extensions for server management, improved security measures, website creation, etc., and there are a lot of additional third-party add-ons to choose from. With cPanel, users can download extra apps via auto-installers through the app store, which is carefully managed and verified by official support.
Why is cPanel used?
It is used for many reasons. The most popular ones are because this software offers:
- A simple GUI. Without a control panel, you have to execute everything on the server through a command line. cPanel users only have to have minimal knowledge of website and server management as everything can be done with a few buttons on a simple web browser interface.
- Easier website maintenance and domain management. With a cheap cPanel license, users are permitted to install additional applications, add-ons, extensions, and software that automate repetitive server tasks and allows them to quickly create and customize webpages. Such features as Zone Editor, Site Publisher, Aliases, Redirects, and Subdomains make domain creation and handling tasks quick & easy.
- Improved security. It boosts website and server protection with such integrated tools as IP Blocker, Leech protection, two-factor authentication.
- Great file management. You can upload, create, remove, and edit various files through the file manager without the need for third-party applications or FTP.
- Database management. It also allows users to create and interact with their databases with such tools as phpMyAdmin or phpPgAdmin and has MySQL and PostgreSQL Database Wizard interfaces for handling large amounts of data.
- Helpful email functions. Users can make their email experience easier by using such integrated tools as forwarders, email routing, autoresponders, mailing lists, filters, greylisting, address importers, calendars & contacts, archives, and even encryption.
- Metric tracking. The cPanel license also grants access to metric tools that allow you to track everything happening on your website and server: traffic, visitor behaviour, bandwidth usage, errors.
What is WHM?
Also known as Web Host Manager, it is a server management interface that is part of the cPanel & WHM software suite. WHM grants administrative access to the backend of cPanel and the ability to create and manage multiple websites. With this, users can easily monitor their servers, manage backups and security, create, delete, or suspend cPanel accounts, access DNS zones, and more.
When combined, cPanel & WHM become a versatile control panel with useful features for both simple website tasks and larger, server-wide maintenance work.
What is cPanel?
It is a Linux-based web hosting control panel that provides a graphical user interface (GUI) for hosts. Having a cPanel license grants access to useful features that ease website and server administration & maintenance, minimizing the need for in-depth technical knowledge. It utilizes a 3-tier structure beneficial for administrators, resellers, and end-user website owners.
Because of the intuitive interface, various automation tools, API-based and third-party software access, application-based support, and compatibility with many Linux distributions, this software is now one of the most popular control panels used for hosting.
